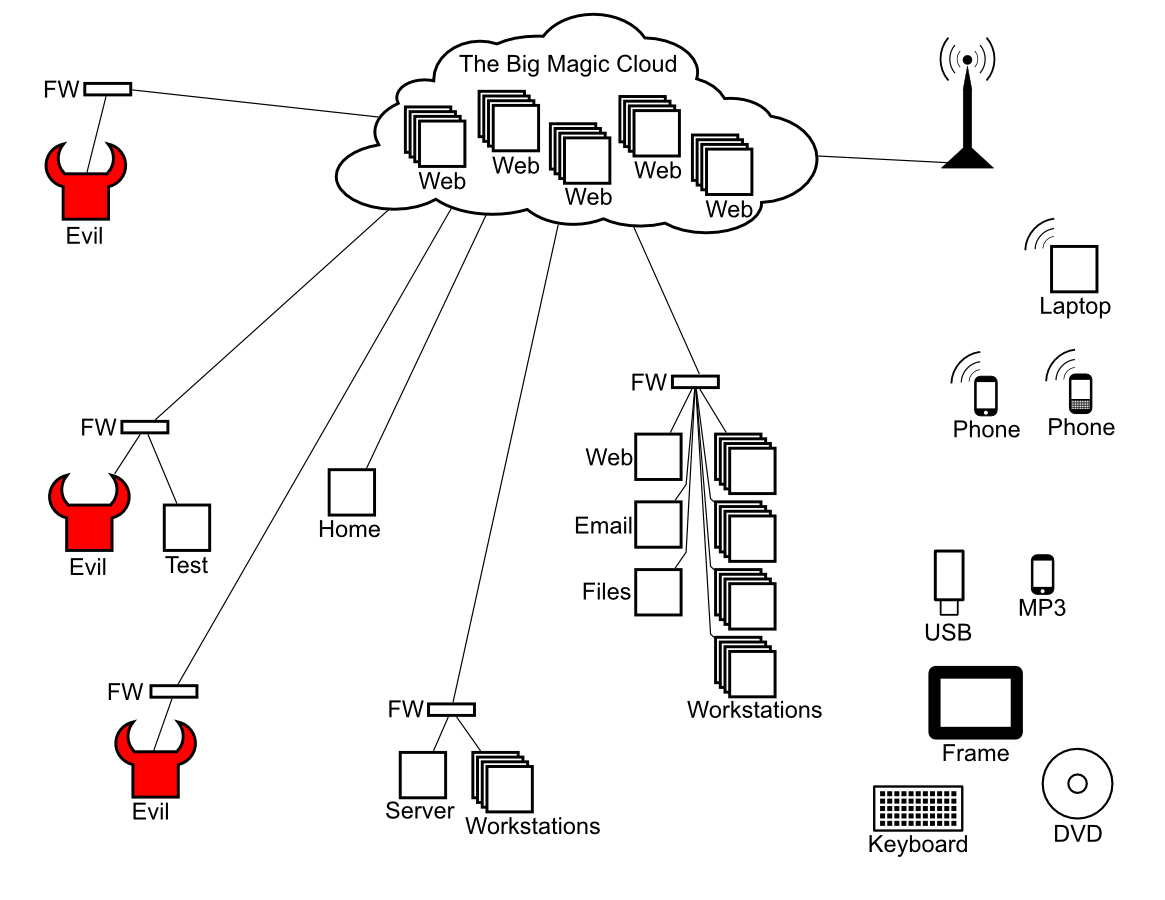
In 2009, I created a presentation on malware that was aimed at the financial services sector. The presentation was based on a pre-drawn whiteboard, and as the presentation continued the attacks were drawn in red. Deemed successful, it was extended into a webinar, but due to the complexities of lining up a whiteboard at meeting facilities and the time required to pre-draw the board it was later replaced with several slide-based presentations.
The graphic used as a base in the webinar is below. Below that are notes for the presentation itself.
- Past: kids for exploration and bragging.
- Today: criminals to make money
- Past: could just run cleanup tools
- Today: far more stealthy, as long term infections make more money
Criminals working together.
- Networks of affiliates, not bound by country
- Russian name for this: Partnerka
- Pay per click, pay per install multi-level marketing schemes
- Malware is brokwn up into parts now, with different groups contributing different “modules”
- For example, one pharmacy scam can net $16k per day
- Referal fees alone can net $180k per year
Price chart (trendLabs)
- Payout for each unique adware installation – 30 cents
- Basic Malware package – $1,000 to $2,000
- Exploit kit rental – 1 hour $1
- Exploit kit rental – 5 hours $4 (Buy in bulk and save)
- Distributed Denial of Service attack $100 per day
- 10,000 compromised PCs $1,000
- Stolen bank account credentials – $50+
- 1 million freshly-harvested emails – $8 up, depending on quality
Malware Families
- Lots of analysis to group malware into families
- This is useless, who cares if it’s a virus or a worm, what matters is how much damage was done
- Enter vector analysis
Vector: Web – Lazy
- Put up own website
- Same problems with driving traffic as regular sites
- Need to leverage SEO
- Sometimes need a hook (often paired with Email)
- IBM reports that malicious links increased five-fold in 2009
Payload: Scareware
- Play on fears
- Resemble anti-malware sites, use colours and shields and everything
- Looks like a scan, but they infect you… and make you pay for the privilege
- Fifteen new sites discovered daily
- Uses SEO, don’t trust search links
Vector: Web – Moderate
- Target a social networking site
- It already gets the traffic
- Users have to be able to upload content
- Facebook Games
- Attackers post content and try to get people to DL it
- Then, when people view it, it runs and posts it for more to see
- Content is viewed as “safe” when it’s not
Payload: Malvertising
- Infect an ad server and get your malware on lots of high-trust sites
- Got New York Times and Van Morrison last year
- Adblock
- URL Shorteners
- (Choose one that cares. Bit.ly has worked with leading anti-malware providers to make it as safe as it can be.)
Vector: Web – Difficult
- Take over popular website
- Most are well protected, but if it can be done, the value for the attacker is high
- They can then load it up with malware and take over all site visitors
Payload: General: SQL Injection internet-wide attack (backend databases)
- Thousands of government sites, fortune 500 companies and schools infected in early 2008
- Sometimes, specific sites targeted, as in April: Paul McCartney
- 7Safe reports that 40% of all web attacks involve SQLi
- The more interesting you are, the more of a target you are.
- Embassies are targeted, to leverage attacks up to high-profile people
Vector: Email
- Anyone can send to anyone from anywhere
- Trusted relationships can be abused via forgery
- Also can utilize a popularity wave
- natural disasters and celebrity deaths (Haiti)
- Elections (Obama)
- Paranoia (Birthers)
- FBI and IRS do not send emails
- Package delays are not sent out (UPS, FedEx and DHL), instead a customer will call
- There are no Internet lotteries
Vector: Webmail / IM / Web Forums
- These can be spammed
- Attackers trafficing in usernames and passwords
- If someone asks you to “retweet”, ponder why
Vector, Payload: FTP / Gumblar
- Take over developer’s workstation
- Track FTP info and login in legitmately
- No way for provider to protect, as all connections look legitimate!
Traditional Attack
- CD, DVD, BluRay, Floppy, media cards, USB
- Compromised from the factory: Digital Photo Frames
- Keyboard keylogger
- Take over a system through the avenues into it
- Cell Phones and MP3 players are risks
- iPhone viruses have been seen now.
- First, just a joke
- Later, the same joke that was leveraged to do something else
Future Threats
- Increased focus on narrow and specific targets
- HTML5 and Google Chrome OS blur the lines between on and offline
- Increase of targetted attacks (happening now, but under reported)
- Mac OSX currently at risk, and will grow
- Mobile device risks will grow
- iPhone and Blackberry being exploited NOW
Just Break In
- Patching
- Microsoft, Adobe, Quicktime, etc
- Firewalls help, but if anything is running, it needs to be patched.
Impact: Data Theft
- What can malware do? Anything.
- It can grab passwords
- search disk for sensitive data and send it offsite
- Steal user names, passwords, account numbers, credit card numbers (ID Theft)
- 2009 Verizon report found that 93% of data breaches were in financial services and 90% of those were linked to organized crime
- Espionage – Google / China (details still coming in)
Impact: Theft
- track access to bank accounts and steal money (Names: SilentBanker / URLZone / ZEUS)
- Blocks logout and does a transfer
- Tracks transfer and hides it’s own activity!
- Is aware of transaction limits and stays below threshholds
- Leverages existing confirmation technology, so 2 factor doesn’t provide protection!
- Money mules
Impact: Take Orders
- Botnet: Ghostnet – over 1000 machines in 103 countries, belonging to government, aid workers and activists
- Botnet: Unnamed – Wire Transfer email infects and starts collecting information entered into web forms, websites visited and directories accessed
- Botnet: Koobface – Registers accounts on social networking sites: Facebook/Myspace/Bebo/Tagged/Friendster/Twitter/Gmail, friends people, sends them malware
- Botnet: Many others – Send Spam
- Since it’s free to use other resources, ANY acceptance keeps it going
What can be done?
- Basic server and network hardening: firewall, disable unneeded apps, layers of defense
- Complete endpoint solution
- Signature-based still needed, but due to polymorphism, won’t take care of it all
- Behavior-based profiling, formerly “heuristics”
- Look for pre-executation, not simultanous execution (race condition)
- Endpoint Firewall – internal pivot protection
- Application Control / Whitelisting – For those who can’t avoid granting admin privs
- Web Browser Helper Objects – Javascript
- Zero Day Protection (define, look at independent tests)
Optional
- Encryption – protect against casual data theft, not perfect, but does add a layer
- NAC – connect with network infrastructure. Still difficult to implement. Look into your infrastructure
- DLP – Look at the data and prevent it from crossing boundaries. Right now, it’s a nice to have.
- Reporting – If you’re regulated, reporting is important.
- Lightweight, Frequent Updates – fast updates are essential as new threats emerge all the time.
- Time Tested – Some new players that are promising, but also a long history of new players that don’t make it.
- If you’re in a business, it may be better to play it safe… at least until you know the company is stable.
- Keep the scareware threat in mind and research carefully
Mild Concerns
- Company Operations – For security software, look at support and responsiveness. If they offer to save you money by reducing service levels, be very careful.
- Home Use – These days, home users connect in all the time. You must protect against this somehow.
- Mobile Use – As time goes by, mobile devices become just as important as home use. Be prepared.
- Multiplatform and Legacy – It’s best to protect any legacy systems you have. Ideally, this wouldn’t require secondary systems.
Conclusion
- If you have money, you’re a target.
- No solution is perfect
- Make sure you lock things down as tight as you can
- Supplement with antimalware
- Plan for failure
- Fix your apps!